Brian Krebs- KrebsonSecurity¹ has a story of Cici’s Pizza with a data breach on June 3rd .
This credit Card breach story is interesting but not what I want to discuss.
Instead let’s discuss “Todd”‘s response in the comments
1st response:
So obviously Todd wrote this response as an immediate reflex action and does not have an understanding of how Internet Cybersecurity works.
He keeps trying to impugn the integrity of Brian Krebs and reduce the actual faults (which he acknowledges) on his ‘placeholder’ website.
This is the problem Todd: Even a placeholder can be an attack vector and obviously Todd does not understand this. Also have you heard of watering hole attacks? Where a website is attacked and compromised, the subsequent visitors on the website would then get attacked not knowing that happened.
Almost like saying please hack us we don’t pay attention to this site (last updated in 2012).
The other thing is – when PR is concerned if you don’t know what to say – saying nothing is better.
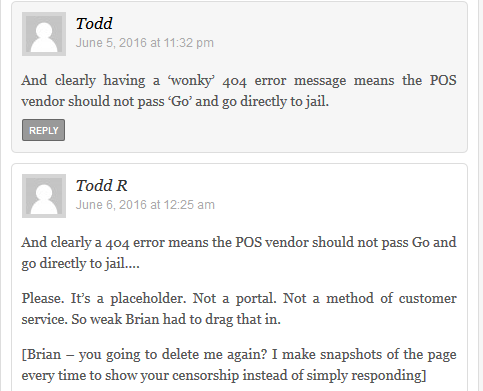
Now let’s go to Todd’s 2nd response:
This response just confirms Todd’s inexperience and naivete.
But the worst is yet to come….
Yes – 3rd response:
His last response does all the wrong things again – admits to not caring about their website and so what if we had adware injections to potential customers or our customers.
The third response proves that his responses are just reactionary and not well thought out – even though the first started June 5, 2016 at 1:45 pm then 2nd at June 6, 2016 at 12:25 am with final at June 5, 2016 at 10:47 pm (so obviously the responses were quickly being sent while Brian was making sure this was not spam and he finally allowed them to go on the site) But there was at least 9 hours and finally almost 12 hours between responses (explains why there were no substantive changes in his response)
Even though Todd claims to be part of a POS (Point of Sale) technology company apparently Todd believes there is no correlation with being up-to-speed with your unimportant (in his eyes) website that discusses POS technology. Confirming it was not updated for 4 years is not a plus.
Also claiming to “have a home page” because we have to have one. Misses the point of cybersecurity. You must protect all your assets not just the ones 1 person is aware of.
Or at least fix them, update them on a regular basis. Not every four years (i.e. when we get around to it).
So what can we learn from this Todd vs Brian exchange?
I would say do not try to engage with journalists even if they are wrong unless you have a crafted response and stick to your points.
the points should not be
A. We did not do it that badly (this is a bad argument on all accounts)
B. Our xyz property is not important – and none of our customers got hacked as a result of our mistake.
It is better to figure out the right response and maybe even ask someone else before actually responding.
Forgive me but I want to point out the obvious – Saying we did not screw up so bad is not what should be said. If you will accept blame apologize without saying someone else is at fault. then fix the problem ASAP and say that.
Tell us how you will keep things together in the future, don’t start arguing with the journalist on minor semantics just to win a small battle.
But most of all remember to do risk analysis and the following concept(your limited impact items are likely already hacked – and thus the attacker is already in the network trying to attack more interesting targets):
And more info in this past post² (Feb 8th, 2016)
So contact me to review your “non-essential” properties before they get hacked.
Finally – realize that the Internet is 24/7/365 – if you don’t get that would you accept no more Netflix at 2am on a Saturday? It is at 2am when you get attacked. Don’t whine about writing a story on Friday and needing a response at 2pm on Friday. Now we know why your company has problems.
Also it looks like Brian’s comment software had a hiccup in orienting the comments when Brian took a little while (Friday evening) in sorting the comments once approved. I took them to be 1st , 2nd , and 3rd responses as they are listed top to bottom.
- http://krebsonsecurity.com/2016/06/banks-credit-card-breach-at-cicis-pizza/
- http://oversitesentry.com/not-patching-in-time-can-hurt/