The latest information about a Romanian hacker getting into the ” Hillary Clinton server” interests me. The hacker claimed that hackers sometimes do not leave a trail. So I don’t want to focus on whether it happened or not(or the ramifications of he hack – politics etc). Just on the comment of not leaving a trail in the logs. NBCNews¹ has a story on this topic.
What is interesting to me is that logs can be tampered with or a hacker’s tracks are not made with some actions.
How can logs be tampered with? In Linux/Unix one can delete lines if one has administrator(root) access.
The problem is once a hacker has root access they can modify files and even insert other programs into the computer which can compromise the computer from then on. there is a good back and forth on Splunk² answers page.
The log files can tell us what is going on the machine and even log file tampering can tell us that all is not well.
Keeping track of history of the commands executed on a Unix machine is also good.
On all machines we are dependent on keeping administrator access out of the hacker, since if they can modify any file at will, add and subtract files from the computer the game is over.
Also what will happen is rootkits will be installed on computers that the hacker can access with admin rights. Rootkits are bundles of programs that are created by hackers for various reasons, usually to continue the ability of the hacker to control the computer.
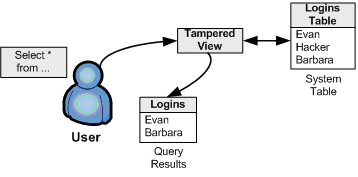
The image above is from docplayer.net³ a presentation on SQL Rootkits and Encryption by Kevvie Fowler.
It seems the SQL rootkit can modify login information, expertly maintaining unauthorized access while making it look like standard processes are working.
a rootkit can modify any of the following:
- Logins and/or users
- Processes
- Executables or files
- Registry entries
- Active ports or services
The report goes on to say that there are 3 generations of rootkits out in the world now (also considered ‘out in the wild’)
The third generation directly alters the content of memory allocated by the RDBMS (Relational Database Management System) i.e. the SQL server itself.
This is most profound as now the hackers are not just changing files, but now the server instances will be modified by changing the memory allocations for the server. This makes the problem of finding rootkits that much harder.
More to come on this subject.
Contact Us to discuss ways of “Rooting out Rootkits”.
- http://www.nbcnews.com/news/us-news/shootings-two-maryland-malls-kill-two-injure-two-police-n569411
- https://answers.splunk.com/answers/27071/unix-log-file-tampering.html
- http://docplayer.net/6399081-Double-trouble-sql-rootkits-and-encryption.html