
 | |
 |  |
| Saint Louis Metropolitan area Phone: 314-504-3974 Tony Zafiropoulos |

| |
 | Book on Innovating with IT - Tony Zafiropoulos 8/1/2009 --- TonyZ Resume
LinkedIn profile --- Twitter Feed Fixvirus |
I have been very busy helping upgrade a windows 2003 network to Windows2008, recovering a Windows2008 server, and working on the Swiss Authentication Search engine optimization project as well as creating a new blog for Swiss Authentication. in Blogspot. Blogspot is joined at the hip with Google.
Search for "Authentication Marker" in Google Swiss Authenticaiton is #1 :)
Tony Zafiropoulos
6/30/10
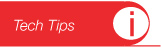
Fixed a very nasty malware - called the XP Defender Pro, I tried to clean it, but after an hour of various methods (including installing Kespersky Anti Virus.
The safest method after the hour was to re-install WIndows XP.
Here are the pictures of the virus/Malware - very tricky makes it look like legitimate Microsoft software.
Fortunately customer did not give them any money - due to the software asking for Rubles.
It even has a display icon
![]()
Which is by the tray in the right lower corner of your computer screen.
Notice also the way it claims to find infections. - XP Defender Pro is not a legitimate product - it will de-activate many regular usages of the ocmputer. On this computer the associations of icons with their programs were removed. So you could not click on any program directly. (I was able to run things by going to the directory the program resides and running it from the DOS screen). Rather unwieldy for most.
Tony Zafiropoulos
4/1/10
Have been very busy - installing an Avaya phone system - Partner Plus, customer bought a phone system from an in-city wholesaler. Wholesale Telecom IncIt was a 3 line system with 8 extensions.
The installation went smoothly, the programming to how the customer wanted the phone vectors is what took a few hours.
I worked on early versions of Partner (v1.0, v2.0) this was v6.1, and apparently a lot of changes occured in the last 12 years or so. It took a while to figure out the correct voicemail and ringing setup. but now the customer is happy.
Another current project is setting up a Windows Server2008 plus Exchange Server2007. In a small business server setup.
Tony Zafiropoulos
2/15/10
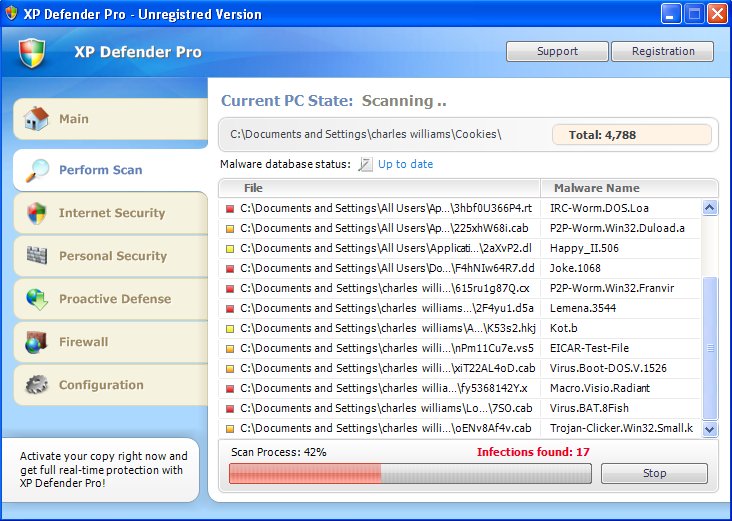
Fixed another Virus the Psecurity virus.
It was located in C:\Program Files\Personal Sec\psecurity.exe
It was relatively easy to turn off, just start in Safe Mode and find it - found in registry the pointer to the files above.
This virus does not start in startup area in msconfig (only in registry).
Tony Zafiropoulos
1/05/10
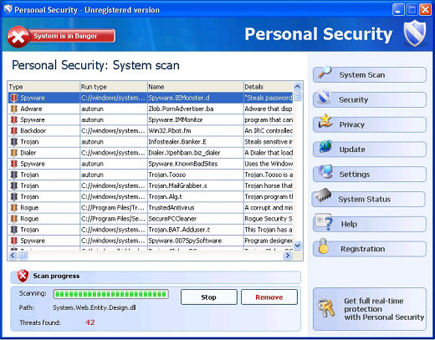
Fixed another SecurityTool virus infestation. This one is rather new.
Do not pay these guys- ithis is a virus not a security tool :)
today's virus was located(Windows7 machine) in:
C:\Programdata\43299834\43199834.exe
also had the following registry key:
HKCU\Software\Microsoft Windows\CurrentVersion\Run
a couple of days ago I fixed the Security Tool on WindowsXP system:
%UserProfile%\ApplicationData\494655101\494655101.exe
Registry key: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
The key was to reboot into safemode, start msconfig and uncheck how the virus starts itself.
If it will not let you do that, then you have to reboot, while booting and before explorer is fully running, start task manager (ctl-alt-del) end the explorer process, then run msconfig and uncheck the virus, once you can do that you can start the system and delete the virus.
I suspect this virus is morphing, and also may not have the same signature and saved files every time.
That is ok, it has the same methods though, it has to start like all other programs, and then you can find where it is located, wither in a user profile, or c:\programdata or some other folder.
After working on viruses for 14 years these items come naturally :).
Tony Zafiropoulos
12/30/09
Ok, I guess it was too drastic a change for Microsoft to allow their biggest money maker not to be sold starting Jan11th.
Here is a Yahoo news story
Which says Microsoft will fix their software so as to accomodate the lawsuit, and thus being able to sell all Word software after all.
Tony Zafiropoulos
12/29/09
Stop the Presses!!!
You can't buy Microsoft Word Starting Jan11, 2010.
Yahoo News Story about the head turning news.
Make sure that you have enough Word for your new computers or you can download
Openoffice which could turn out to be the saviour.
Tony Zafiropoulos
12/22/09
Three interesting developments in the Global anti-virus front:
1. CSOonline has a Story about a Rogue Google search results; here are relevant items in story:
"I see this all the time," he said. "Poisoning a trend is nothing new, but in this particular case, it's a search where you actually click on Google's logo and you get results back from sites where half of the links have been compromised."
A Google spokesman said that this type of problem affects other search engines as well. Google is aware of Tuesday's Doodle problem and has "already removed many of these sites from our index," he added.
"To do this, we have manual and automated processes in place to enforce our policies," he said. "We're always exploring new ways to identify and eliminate malicious sites from our index."
2. Adobe will not patch a Zero day vulnerability until Jan12th
12/16/09 - Adobe won't patch the newest critical vulnerability in its PDF viewing and editing software for another four weeks, even though attack code has been publicly released.
This is a problem with any manufacturer that is not open source.(TonyZ)
3. Chinese ISP hosts 14% of Conficker virus infections
In terms of the total number of infected computers, China Telecom's Chinanet seems to have been hardest hit by the worm, which began spreading late last year.
The Chinese ISP had more than 1 million infected systems within its massive 94 million IP address network. That amounts to just over 1 percent of the company's network. But while Chinanet has the most total infections -- amounting to about 14 percent of all known copies of the worm -- it doesn't have the highest percentage of infected systems. Other, smaller ISPs show up on Shadowserver's list with infection rates as high as 25 percent.
It is interesting to note that likely all ISP's have a large number of infections, China Telecom is just a large ISP which is still working on ways to mitigate these virus threats.
Tony Zafiropoulos
12/21/09
Helped move a small company - 8 computers(Windows7) and a SBS Windows 2008 server.
There are a lot of similarities to Windows 2003, and Windows Vista for the respective OS's.
It was relatively straight forward. Windows2008 Whats new page on Microsoft's site.
Tony Zafiropoulos (12/13/2009)
The site was crawled on 11/23/09 (before that it was 11/22/09)
It looks as though the site is being crawled daily now, although on a one week lag.
Tony Zafiropoulos (12/1/2009)
For the Swiss Authentication website:
One of the combinations of keywords I have been working on is "Authentication Marker", today on Google we hit #2, one of the reasons is that I added the Swiss Authentication webpage Authentication Marker (was called "Marker").
It did take another week before Google crawled the site. -
Just goes to show a concerted effort of Search engine Optimization produces results.
Tony Zafiropoulos (11/27/2009)
This site (fixvirus.com) itself made the #1 spot.
On 11/25 the site(Swiss auth) was crawled on 11/20
The Swiss Auth blog was crawled last on 11/22
The Fixvirus.com site(which made #1 "Authentication Marker upconversion" was also last crawled on 11/22
Tony Zafiropoulos (11/27/2009)
try it, place "Authentication Marker Upconversion" in Google: Click on this for easy googling :).... Number one with upconversion added to authentication and marker.
Also Google now crawling the site every 3 days.We have also added more pictures and more pages, so we are working on getting Google to check the site every day. Also working on getting other blogs to check the site out.
If more sites linked to the site that would make the site more relevant, thus giving higher rankings.
On 11/12 the site was crawled on 11/7
On 11/8 the site was crawled on 11/4
On 11/4 the site was crawled on 10/31
On 11/3 the site was crawled on 10/30
Tony Zafiropoulos (11/13/2009)
Google link with keywords
Specifically the 'Counterfeit Product Authentication Markers' keywords.
The Site is now being crawled more frequently - the last time it was crawled was on 10/26.
When I checked on 10/29 it was 10/25. So in a short time, as long as the site changes daily Google should start to check the site every day.
Also the other keywords are ranking higher and higher, for example instead of the 4th page or 8th page (a few weeks ago) today it is the third page.
The key is to make relevant posts, with interesting information some unique content. And over time it will happen.
Tony Zafiropoulos (11/1/2009)
Regarding my SEO www.swiss-authentication.us project:
I did it :) First page on Google - ranking number 8 using the keywords 'counterfeit products authentication marker'.
You can check yourself :) Google link with keywords
regarding more information about this project - the Swiss Auth Blog link is what made it.
the Blog page has a cache date of 10/7.
So this particular keyword combination worked with that ranking.
When I googled Swiss Authentication the latest cache in Google about the website is actually 10/20 now.
So, essentially about 2 months of working on the site I was able to crack the first page in Google.
It looks like Google is crawling the site every week, on Tuesday. Tony Zafiropoulos (10/27/2009)
Continuing to work on SEO project Swiss Authentication:
I am also checking on Google's crawling frequency:
Last times the Swiss Authentication Website was crawled
10/13 The Main Page with the latest domain name (.us)
10/7 The Blog (the new .us domain)
9/30 The Twitter post about Swiss Authentication
9/15 The Anti-COunterfeit solutions page (with the old domain usa.net)
9/5 The early contact us page (old domain usa.net)
It is interesting to note that in doing Search engine optimization for Swiss Authentication, I am of course trying to
get ranked for other keywords than the company itself, but this way I can actually figure out some of the Google characterstics
So what I did was search for Swiss Authentication in Google and then click on the cache lin, which tells me the last time Google
checked the page and placed it on Google. At some point at the end of September we added the .us domain name (before that there ws only the
SwissAuthenticationusa.net. So a few pages from both domains are on Google, although today they are both the same(the Swiss-athentication.us
is the primary now).
I am updating the Swiss Auth Blog regularly with news of counterfeiting and anti-counterfeiting information. This way the site looks and is dynamic in the eyes of the viewers as well as Google. Tony Zafiropoulos (10/21/2009)
Added a Favicon to the Swiss Authentication website, and since we are using Microsoft's Office Live system, I had to add some code to each page From the Olbtips.com website.
![]()
Notice I made my own favicon to my page -- fixvirus.com:).
Tony Zafiropoulos
10/8/2009
I am now teaching a third class to teach at ITT Technical Institute in Earth City

It is IT222 - Windows Server 2003, this is the class, book, and lab work that one does before taking the MCP certification test for Windows2003.
essentially, installing Windows2003, active directory, replicating Domains, and much more with global policies etc.
The other two classes are of the same class material - IT250 (just different times in the week)
Tony Zafiropoulos
09/28/2009
My latest Project: Swiss Authentications USA is a website on a company that can handle your product authentication solutions.
Anti-counterfeiters beware, it is impossible to counterfeit products with this Marker and reader solution.
Tony Zafiropoulos 09/15/2009

How to crack WPA/WPA2 ... yes WPA and WPA2 can be cracked. And this link goes to some detail on the road to cracking the WiFi WPA protocols.
Short story of article? Make sure your passwords are difficult to guess as brute force attacks work on WPA technologies, and if your password is difficult to crack that is your best defense.
I.e. upper and lower case, as well as numbers and special characters.
Tony Zafiropoulos 09/07/2009
Check out Skype hacking sourcecode Skype Trojan sourcecode I love Skype, but realize it is not secure -keep that in mind fellow netizens
Tony Zafiropoulos - 08/26/2009
Mashable.com says
It seems eMarketer says 6million registered users on twitter (3.8% of Internet)
It will double by years end and increase another 50% 2010. (08/13/2009)
 I know this is "old" news as SANDISK released it's 32GB SDHC on Jun 25th 2009, Press release of SANDISK
I know this is "old" news as SANDISK released it's 32GB SDHC on Jun 25th 2009, Press release of SANDISKbut it is another indication that technology will supercede company policies if one is not ready for the ever changing technologies -
The Wii will accept SD cards but not SDHC cards, as it has to compress the images to show them on the monitor, but I am sure it will happen, especially as the SDHC or the next iteration will become more capable.08/13/2009
New Baseline Magazine issue Keeping the lid on Risk article
Risk About the new compliance challenges that government is creating $1.2tril in added cost. 08/12/2009
Archer Technologies: excellent Governance, Risk, Compliance platform: Use your handheld device to access business continuity data.08/11/2009
Security vigilance never ends combination of products & process improvements -Blue Coat with a proxy filter helps: Blue Coat website08/10/2009
In the technical document section there is a nice document describing the Nmap Scripting Engine. I have extensive experience with Nmap and many other scripting tools.08/07/09
1. Covering the right amount of data
2. Repeating a backup (every day - or every week)
3. Separating the backup from the computer room (the same calamity occuring to the computer equipment can happen to the backup).
4. Many copies of data, make and keep several copies of backups.
5. Test the backup - check the files manually and automatically with verification software.
6. Secure the backup - make sure there is a verified chain of custody ownership trail of documentation.
Am teaching Linux IT250 ITT-Tech fall quarter (fall 2009).
Symantec Support for Enterprise
Many support documents - including the new Symantec Endpoint Protection installation guide(ver11.0)
Remember to always upgrade your Anti-Virus software as quickly as you can, which means of course proper testing (as it is outlined in the installation Guide)
Symantec Endpoint Protection Manager consists of two Web-based applications. One Web-based application requires Microsoft Internet Information Services, which must exist before you install Symantec Endpoint Protection Manager. The other Web-based application runs on Apache Tomcat, which is installed automatically. Symantec Endpoint Protection Manager includes an embedded SQL server and database, and the Symantec Endpoint Protection Manager Console. You can install the embedded SQL server and database automatically, or you can install a database in an instance of Microsoft SQL Server 2000/2005.
The issue is that new versions are better able to handle new threats (with heuristic software) Also version 10.0 has some bugs which cause incompatibility problems(and racing - 100% CPU usage conditions). Tony Zafiropoulos 8/8/08
New Google competitor fizzles: Cuil Supposedly can search 121617892992(121 billion) web pages. And Google can search 3.5 billion, but when you search Google something useful actually comes out. Try it and see for yourself.
Tony Zafiropoulos 7/29/08
The video is a link in the Google code Mapreduce project Mapreduce
Tony Zafiropoulos 6/6/08
This will allow programmers to develop software on the web which is fully redundant and Disaster Recovery safe.
Security is another issue, but I guess one can build that into the system.
The beauty is the usage of parallel computing within the Amazon spare cpu cycle capabilities and infrastructure.
Tony Zafiropoulos (6/6/08) Adobe is the latest large - well known entity to get some hacker attention. Using a zero-day vulnerability in Adobe's ubiquitous Flash Player, hacker Shane Macaulay hacked into a Windows Vista laptop to win a $5,000 cash prize at this year's CanSecWest Pwn2Own challenge.
Fortunately The hacker was doing this for a contest and not trying to steal peoples identities.
Symantec and the rest of the security firms are having a tough go of it in the financial markets. SYMC Symantec had to cut jobs etc.
If you ask me the shoddy software that has been developed is the reason Symantec is having problems.
There are always problems installing Symantec software, it is diffcult to uninstall the old software. Some of this problem is due to the nature of viruses and malware, making the computer very difficult to work on, but customers do not care about this. they just want to use their computer (just like in South Park yesterday).
It was a bit funny how South park represented the Internet, and when the internet went down they visited a large blue router (looked awfully like a Linksys router ;).
But the truth is that everyone just wants to use the Internet, and they do not want to have to mess with their computer (popups and viruses).
The nature of the computer causes this problem. Since it is so easy to install new items malware and viruses find themselves also easy to get installed.
Open architecture and all.
Tony Zafiropoulos 9:35pm CST
Also:
The IT security sector has been clobbered by a frantic pace of acquisitions, increasing commoditization, a fragmented market and competition from a large number of startups even as it adjusts to new threats and challenges such as the recent push toward a war on terror in cyberspace.
Most publicly listed IT security companies have stumbled over the past 12 months, resulting in poor returns for investors from the big names in the space.
From thestreet.com
Our highest priority is to satisfy the customer through early and continuous delivery of valuable software.
Welcome changing requirements, even late in development. Agile processes harness change for the customer's competitive advantage.
This may seem simple - and you may ask... doesn't all software do this?
Unfortunately not
When one programs for a living, one sees that frequently programs are not what the user actually wanted nor can use as they first envisioned.
The problem is that software written in the standard waterfall model, may be easy to 'manage' but does not create what the user envisioned. whereas in Agile Programming the user will be involved almost every step, and thus will have a heavy hand in what will actually happen.
Tony Zafiropoulos 4/15/2008
This is interesting as this could be the underlying infrastructure for what is called "Grid Computing". This is where one just buys the hardware resources on uses instead of computers, software, internet connections, etc. Tony Zafiropoulos 04/08/2008
Google announced the introduction of Google Sites as part of Google Apps. This is a nice addition to the free suite of Google Apps services. Here is a brief introduction to Google Sites:
I have create a basic site: Tonyz share
"Of course, this begs the question of security. Android's basic security model against standard malicious code is a prompting model. Applications must include a manifest stating what sort of potentially dangerous features they want to use, such as making phone calls. When installed, the user will be prompted (or possibly some other authority will be queried in the case of signed code) and forced to decide if the application should be allowed to perform some operation. In contrast, Apple's iPhone has currently taken a reverse model approach where third-party on-device applications are not allowed, preventing the vast majority of malicious code for the average user.those that haven't unlocked their phone."
How Android handles security will matter, but Symantec must realize that Linux has some inherent malware blocks - of which anyone with a modicum of Linux knowledge would know. I.e. permissions and ownership is inherent in the operating system.
How applications are developed and in what space in the operating system stack they are allowed to live in will matter. But it is not hard to make the system secure since Linux has inherent infrastructure (Android is built on top of a Linux lite). Whereas trying to make a Windows OS secure is much harder, since it is built on the principle of allowing programs to run in many diffrent spaces.
Tony Zafiropoulos (2/12/2008).
Rumors are circulating that Dell and Google will use the Android platform to launch a new, Dell-branded cellphone at the 3GSM conference in Barcelona next month. The handset, which would mark Dell.s return to the mobile device market after they ceased creating PDAs, would leverage Google.s online application suite in what would likely be a cost-effective device.
Are you aware of the Open Handset Alliance?
This is their FAQ as of today:
What languages does Android support?
Android applications are written using the Java programming language.
Can I write code for Android using C/C++?
No. Android applications are written using the Java programming language.
Will Android run on insert phone here?
No.
In a general sense Android is an effort by various interests (including Google) to develop a phone that will work in many different networks (AT&T, Cingular,Deutsche Telecom).
The effort could rework the Cell phone industry. Tony Zafiropoulos - 01/13/2008

This spam is an interesting new twist of political spam while using a new ingenius method of dissemination, as outlined fromt the link above:
"While the total count of Ron Paul spam messages that actually landed in peoples' inboxes can't be known, it certainly was received by millions of recipients," writes the author of the SecureWorks report. "All this was done using around 3,000 bots.this speaks to the efficiency of the template-based spam botnet model over the older proxy-based methods. The front-end also plays a part in the efficiency, by allowing the spammer to check the message's SpamAssassin score before hitting send, simplifying the process of filter evasion and ensuring maximum delivery for the message."
Although it's likely that somebody paid nenastnyj to transmit the Ron Paul spam, there is no evidence to indicate that it was anyone directly associated with the Ron Paul campaign.
Tony Zafiropoulos 12/7/2007
Wyse terminal management strategy.
It is interesting what Wyse says about this infrastructure:
By doing so, Wyse thin clients work seamlessly with a broad set of management tools allowing IT administrators to centrally monitor and control networked devices in the environment they are most comfortable with.
Wyse was referring to the various third party apps that run the thin-client architecture (Citrix® Access Management Console, Altiris® Deployment Solution., CA Unicenter®, IBM Tivoli® and Microsoft SMS® (Systems Management Serverver)
Tony Zafiropoulos 11/19/2007
![]()
Working on another large project - which will be occupying my time in the next 2-3 weeks. VMWARE ESX installation. In the coming weeks I will discuss the installation and configuration of vmware.
Current Book I am reading: VMware ESX Server so far so good has excellent overview and introduction.
Of course for up-to-date information you must visit the vmware and VMGuru website
Tony Zafiropoulos - 11/16/2007
![]()
Moore's Law is now 40 years old.
The "law" was adopted after Intel co-founder Gordon Moore wrote in a 1965 article that the number of transistors on a chip would double every 24 months.
Dr. in article)Moore (now retired) answered a few questions as to the origin of the "Law":
"I looked back at the few preceding years and saw that we had about doubled every year.
I took this doubling every year and extrapolated it for 10 years to say the complexity of integrated circuits would go from 60 to something like 60,000 on a chip. "
A very interesting interview - at the end he is very skeptical of Quantum computers.
The problem is that most inventors and geniuses (Albert Einstein as well) cannot see very far into the future... There is no place else to go but quantum, it may take a while but once it gets going there will be no stopping it.
A Quantum computer will break all encryption methods, where it will take hours and days for a silicon chip computer to break enryption codes, the quantum computer will take minutes.
If there is a will there is a way: The drive to break encryption codes will usher in the age of quantum computing. Tony Zafiropoulos (11/11/2007)
![]()
11/06/2007
Finally have some time to make more posts... Someone contacted me and asked if I give a conclusion to the phone system decision that we had (between Inter-tel and Avaya IP Office500).
We went with Avaya IP Office 500... and the reason was that Inter-tel had a limitation with Internet VOIP communications - it would take twice the resources (channels) within the voice processing unit.
Initially it would not have mattered for us (60 unit installation with few internet connections - if any), but as we grew and with time it possibly would have made a difference, and I was looking for a technical difference between the two, since they were very equal.
I was impressed with the Shoretel product line, but it was more expensive and management was not comfortable like they were with Avaya's track record.
We have been happy with the Avaya IPOffice500 so far -- we switched from an old Executone system, so this was a big jump. initially we did not have the same capabilities, but after some cajoling the company that installed the system finally gave us a lot of the same features we had before.
The only thing still missing is a ring on a second call (same phone) ... The receptionist was used to the second line ringing, not just a brief chirp (abbreviated ring).
But on that feature and a couple of others we have created a work around (we bought a bell), so on the whole we have not settled, and I feel that we got a good deal. Tony Zafiropoulos -- 11/6/07
![]()
Free Email digital certificates
Everyone should be required to get an authentic digital certificate --- if you do not have one, ythen you cannot send legitimate emails.
Tony Zafiropoulos (10/08/2007)
![]()
SANS Internet Storm Center Diary
This is the snippet:
As the Anti Virus industry moved a step forward and improved detection of obfuscated exploits, the attackers started a trend of creating obfuscated exploits on the fly. I wrote about this before when I encountered dynamic JavaScript obfuscation (see http://isc.sans.org/diary.html?storyid=3219) every time a client requested the web page containing exploits, the server side PHP script picked random variable names that, in this case, caused the whole function to be different since it was using the infamous arguments.callee() method so it depended on the function body.
This is not a good thing as it means the Anti Virus vendors will not be able to catch immediate future vulnerabilities and things will thus get interesting.
Tony Zafiropoulos - 10/1/2007 Oh and interesting note - the Symantec Anti-Virus program was causing the problem on the Thinkpad below... I will have to uninstall and install a new version of AV software.
![]()
Received a thinkpad tablet PC, that has an interesting error...
"debug assertion failed" Whenever Internet Explorer is attempted to be used.
I tried uninstalling a few programs, It also had a C++ error indicator. possibly within the IBM security software.
Fortunately I had Mozilla installed so the client can use the PC still.
Hopefully I can fix it without reinstalling Operating System.
Tony Zafiropoulos 09/21/2007
![]()
I was at the Skandalaris Center for Entrepeneurial Studies event yesterday:
SCES website
An excellent speech by an innovator: Mr. Mehdi Ghameshi.
How to differentiate:
Culture
Customer Experience
intellectual Capital
--Directors
--Assciates
Products & services
Capital
Technology
Cost effective physical structure
He is the CEO for GreatFloridaBank
Mission: GFB provides ideas and solutions to our customers financial needs.
Culture of success:
++Pay for Performance
++Motivating Leaders
++Do it right the first time mentality
Each customer is guided through their experience by only one associate.
The bank was put together from scratch 5 years ago into $1.7Bill in assets, the number 5 bank in Florida
Because I am interested in innovation and how it occured, he said that he got ideas from traveling to Europe and looking at how people did things there.
He is very interested in pay for performance and listening to the employees at the lowest levels - he believes that is where most of the innovations come from - ideas come from the customer service rep, not from the CEO.
Tony Zafiropoulos 09/21/2007
![]()
We need an email revolution - (not evolution), because spam has reduced the value of email in general.
So, here is the Mozilla group: Newslink
trying to overhaul email/Internet communications.
relevant snippet: "Currently, the company that owns most of the world's mailboxes - Microsoft - has done little to nothing to improve the email experience. Email today is essentially the same as it was 10 years ago. This is almost criminal, given how much time we spend in it.
A good friend with access to Microsoft's Exchange team suggested a reason for this, which came from Microsoft: the Exchange code is so old and so crumbly that Microsoft doesn't dare to fiddle with it. Yes, it would make perfect sense to centralize collaboration and social networking in the address book/email client, but Microsoft apparently can't do this without risking the stability of its omnipresent email client and server."
Software development has inherent problems as it ages. It is good sometimes to start anew - even if the effort costs a lot in resources.
Tony Zafiropoulos 9/18/2007
![]()
Interesting Site - they are logging malware and hacking attempts to a honeynet project on the net.
A honeynet is a system that was designed to view the activity of hackers and other malicious programs
It is a good tool to see what is going on in the wild Internet.
Malware logging site:
They are using a program that they developed called bothunter.
Tony Zafiropoulos (9/17/07)
![]()
My favorite website for checking the status of the Internet SANS:
SANS Internet Storm center article
This is an excellent article about whether to use Anti-virus programs in the future.
The problem is that AV vendors are having a hard time keeping up with all of the new viruses and malware products. Especially when there are new viruses which are not detected by virus filters.
Until the AV vendors fix the new viruses by including them into their filters there are a certain amount of viruses in the wild even with AV software installed. (therefore the safety by having an AV product is not all that safe)
A behavioral approach needs to be investigated says Mark Shearwater. I will agree with this assessment, as perfectly good machines (with AV products) have received malware/viruses.
People contact me all the time with virus issues even though they run AV programs.
We need a better prduct with Heurestic abilities, able to analyze and predict new methods of attack. Symantec, McAfee are not doing a good enough job.
Tony Zafiopoulos(9/4/07)
![]()
9/4/07
I just ran into a weird computer issue:
Symantec website link about a Dell Optiplex745 model that places itself into a weird mode where the monitor will go dark after installing Symantec Antivirus.
From Link:
Symptom: Dell Optiplex 745 computers cannot start in normal mode after you install Symantec AntiVirus 10.1.
You install Symantec AntiVirus 10.1 or Symantec Client Security 3.1 to a Dell Optiplex 745 computer with a dual core chip. When you restart the computer, Windows cannot start in normal mode.
This has a specific fix associated with it. it may or may not fix the problem, I recommend to contact Dell support and then decide on a relevant solution.
Tony Zafiropoulos
![]()
8/27/07
Fixed two computers in the last few days - one a vista machine that would not run correctly , where explorer was restarting every few seconds not allowing anything to work.
The other computer was yet another Norton antivirus installation that was not upgraded but the definition files were renewed.
Please do not just renew your definition files, one must upgrade the software (from 2006 to 2007 Norton Antivirus for example).
The cost is very similar within 10 dollars, and you get much better protection.
This particular computer (WindowsXP) had a virus/malware that would not be detected by symantec's anti-virus software (the latest version 2007).
I used the smitfraud.exe from this website link
and the trusty hijack This tool that I use frequently.
Hijack This Linka very powerful program that can break many programs on your computer - be very careful on its use.
Tony Zafiropoulos
![]()
As of 8/17/2007 1pm.
Link to Article about Excel Flaw
Check this out:
Microsoft's Excel application contains a vulnerability that could allow a remote attacker to gain access to a system.
The flaw affects multiple versions of the spreadsheet software, including Excel 2000, 2002 and 2003, as well as versions of Microsoft Office containing those versions. It can also be manipulated in Excel Viewer 2003 and Office 2004 for Mac.
Tony Zafiropoulos ---- This only means that we could see potential viruses/malware that exploit this vulnerability.
As usual - please be carefule what you click on when using your email and dont go to websites that you do not know are safe.
![]()
Has anyone noticed a marked increase in spam traffic?
Eweek article about the 4.45 times increase
From article:
The largest spam attack ever tracked wound down Aug. 9 after delivering enough big, fat PDF files to increase total spam size 445 percent in one day, according to Postini, a hosted e-mail filtering company that's been tracking the attack since it started Aug. 7.
It is the weird pdf file emails that say nothing important.
Unfortunately this means that this is just the first phase, many other phases will now come into being. The problem is that these are just the beginning, there will be new and improved versions of this spam - especially if it was successful.
Tony Z. --- 08/12/2007
![]()
June, 4th, 2007
Among other things the next project is a Search engine Optimization tactic of using a portal to increase website ranking for various keywords.
For example if one goes to Google and types: "link:www.yoursite.com" then one will find out how many sites and what is linked to www.yoursite.com.
Google Advanced operators click on this link to learn how effective your site optimization currently is. --- I can help you in dewtermining your current efforts for a small fee (as it can be time consuming).
With a successful website optimization strategy one can increase the ranking of the site.
Tony Zafiropoulos
![]()
Spent several days fighting a variety of worms and viruses - Trojan.zlob is one
of them
Symantec explenation of Trojan.zlob
Unfortunately this particular variant was not caught by Symantec's latest (Norton Anti-virus 2007, I was able to defeat it by using several programs, including AVG and Hijack This. which enabled me to stop the instances from running.
Please be careful, and do not go to unauthorized websites. (Tony Z 06/04/2007)
![]()
May 24th, 2007
Text messaging and email:
Whenever you have to explain several topics at once, it is obviously an insufficient medium.
Sometimes a phone call is good, and sometimes one must see the body language.
SarbanesOxley, higher corporate board governance should make the C-level executives more interested in making sure their information is being disseminated correctly and also that their executive orders are being adhered to.
Every industry is cycling through a form of this methodology.
The industries with direct government proposals and contracts have already been brought through these stages:
1. realization that current methods are inadequate.
2. discovery of what is happening when an executive order is being given
3. maybe we need help to resolve this issue.
Clear concise communication is very important as imprecise communication causes confusion and will eventualy cause employees to develop incorrect ideas and thus their actions may collide with other items .
One also needs to know how and when to use the myriad of methods in communicating.
Email, speech in front of various crowds (including one-on-one), text messaging, abbreviations, phone calls, meetings.
When to joke, when to provide inspiration, morale boosting activities.
And sometimes just in actions as in how to dress (casual, formal, or a mix)
If it is done right the IT department can communicate to the whole company a professional and yet warm attitude within the business.
Thus one could even theorize that the IT department can become the most important part of the company.
Which is why I want to run this department (Tony Zafiropoulos)
![]()
May, 12, 2007 -
Wouldn't it be nice to have an efficient way to uninstall products?
The reason uninstalls are sometimes difficult is that in Microsoft Operating systems the registry is used quite extensively by applications, and little vestiges of programs are seemingly everywhere.
These snippets of code can burrow themselves and make it hard to uninstall when the time comes. For example when Symantec Norton Antivirus is uninstalled sometimes you have to go to Norton removal tools.
Unfortunately this requires a functioning Internet and browser infrastructure to ensure uninstallation. For a non-industry DIY consumer the process of uninstall has now been exponentially increased in difficulty.
And then we receive on May 9th a potential security problem with all of the old versions of Norton Antivirus before 2007. This is a travesty. I agree you must upgrade, but it is ever more difficult to uninstall.
When one makes uninstallation so much more difficult it will cause problems to the user community. It would be nice if the software industry would make products that are easier to uninstall then the current state of affairs. Especially in the security of computers market.
Tony Zafiropoulos -
![]()
Symantec has issued a medium impact security advisory:
Symantec Advisory -- Here is a small snippet:
Overview
A design error in an ActiveX control used by Norton AntiVirus could potentially be exploited by a malicious web site. A successful exploit could lead to remote code execution.
Affected Products
Product Versions Solution
Norton AntiVirus 2005 and 2006 Run manual LiveUpdate
Norton Internet Security 2005 and 2006
Norton System Works 2005 and 2006
Unaffected Products
Product Versions
Norton AntiVirus 2007 and later
Norton Internet Security 2007 and later
Norton System Works 2007 and later
Norton 360 2007 and later
Norton Confidential 2007 and later
Symantec enterprise products All versions
TonyZ editorial: As usual, keep your anti-virus products updated, do not assume a renewal of definition files (subscription) is enough. 05/11/2007
![]()
Another project - my Internet service was very spotty (up and down every 2 hours or so), I determined that it must be in the cables (high-speed cable).
So, I switched to DSL again. I was very disappointed with Charter Communications service.
It is a sad story about the state of cable internet - Coaxial cable has an inherent problem in regards to interconnecting two cables together. -- Sure I could have fixed the cable infrastructure at the house, but this would have taken some time.
We all expect the internet to work, and diagnosing the problem was difficult with the tech support in place. I could have solved this eventually by tearing out all of the cabling infrastructure and re-installing. But this is not a wise investment of time - when there is a viable alternative.
Any one of three item have to be done right, or it will fail. The copper shielded wire(D) has to connect, the other copper shielded wire while keeping the shield intact.
 then the copper outer layer(B) has to connect to the other cable's outer layer.
The connnectors to connect the two wires and outer shielding can be easily loosened, thus causing an incorrect connection.
then the copper outer layer(B) has to connect to the other cable's outer layer.
The connnectors to connect the two wires and outer shielding can be easily loosened, thus causing an incorrect connection.
Whereas for DSL it is a basic telephone connection (2 wires copper to a standardized jack)... Many stores provide many lengths of wire and jacks.
Cable or RG-6 is more complicated as you can see in this picture, and in the explanation. http://en.wikipedia.org/wiki/Coaxial_cable. Phone lines run in just the inner portion of the coaxial cable equivalent... so much less complicated wiring infrastructure = much less can go wrong.
Sorry Charter - Hello ATT. :) Tony Zafiropoulos 05/09/2007
![]()
Current Project --- comparing phone systems: Inter-Tel CS5000 and Avaya IP Office 500
For a specoific application and set of needs.
Tony Zafiropoulos 05/07/2007
Also - check out the Searching on 'online learning' keyword
At same link I have added GoogleMap - I centered it on Chesterfield, MO. It seems that AJAX works differently on different browsers - Like IE and Firefox work in different manners. (Try it ;).
TonyZ 05/01/2007
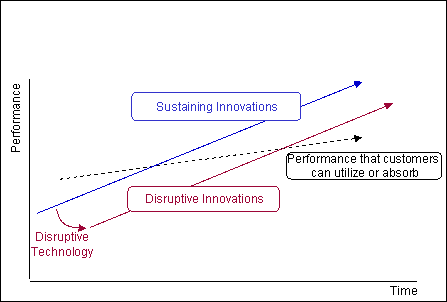
Notice that the Disruptive technology starts out at a lower market capability than the established line, but it too will rise.
The key is to find a market at the lower levels with the future in mind.
Of course it is easier said than done, and depends on your budget - but hte rewards can be immense.
See below on a recent post about more information on the book Innovators Dillema.
![]()
Woman finds error in TurboTax
from a story in Firstcoastnews.com (NBC): OHAMA, NE -- A woman recently discovered a shocking flaw with a website thousands of people use to prepare their taxes.
Instead of taking advantage of this potential gold mine for identity thieves, she is calling attention to it to protect other taxpayers.
Very interesting - who knows how many people were hacked by this flaw?
(TonyZ 4/12/2007)
![]()
Old fixvirus.com webpage - as it looked 05/09/2007
Symantec Hoax list: Do not propagate the hoax 'warnings'. When receiving an email to send to 10 friends check this list first.
McAfee virus list - includes virus map'
![]()
An excellent explanation of the Benefits of Open Source:www.theaceorb.com benefits page Just checked it out, and still a very good reference of how open source programming works ;). 03/2/2006 TonyZ
The Business case for Open Source
SANS Institute incidents.org CID: Consensus Intrusion Database
SANS.org is an excellent group that looks at many security related issues... CID gives a snapshot of current hacker / worm activity on the net.
Anti-Virus centers that we use to control viruses.
McAfee Virus Information Library
This database contains information on more than 50,000 known viruses, including how they work and how to kill them.
Symantec AntiVirus Research Center
Symantec's security update web page - extensive resources and latest information on viruses on the Internet.
Washington Post Chronological History of the Computer Virus