| |
 |  |
 | Saint Louis Metropolitan area Phone: 314-504-3974 Tony Zafiropoulos -- Tony Zafiropoulos resume |
 | Also check my other sites: HistoryStrategy Blog (about historical introspection) --- Sales and ROI -- Ctitek---HobbiesNthings page |
 | Start of my book on creating an IT department - what I learned over 14 years. Do not have a title yet - Tony Zafiropoulos 1/21/2007 |
For a specoific application and set of needs.
Tony Zafiropoulos 05/07/2007
Also - check out the Searching on science keyword
At same link I have added GoogleMap - I centered it on Chesterfield, MO. It seems that AJAX works differently on different browsers - Like IE and Firefox work in different manners. (Try it ;).
TonyZ 05/01/2007
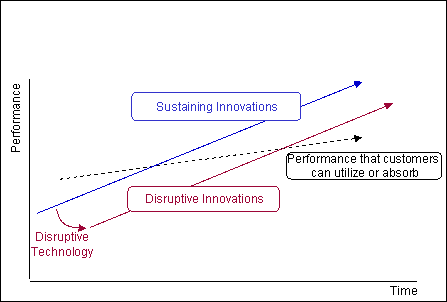
Notice that the Disruptive technology starts out at a lower market capability than the established line, but it too will rise.
The key is to find a market at the lower levels with the future in mind.
Of course it is easier said than done, and depends on your budget - but hte rewards can be immense.
See below on a recent post about more information on the book Innovators Dillema.
![]()
Woman finds error in TurboTax
from a story in Firstcoastnews.com (NBC): OHAMA, NE -- A woman recently discovered a shocking flaw with a website thousands of people use to prepare their taxes.
Instead of taking advantage of this potential gold mine for identity thieves, she is calling attention to it to protect other taxpayers.
Very interesting - who knows how many people were hacked by this flaw?
(TonyZ 4/12/2007)
![]()
Eweek article has the information on the Microsoft Patches that were implemented yesterday. Most of the computers(65+) I manage rebooted after updating with the latest patches.
This is uncharacteristic of Microsoft to create an out of cycle patch, but it could not be helped - dangerous stuff out there. (TonyZ 04/11/2007)
![]()
Innovators Dilemma is a great book with many precise examples of a large company problem - even if they are efficient and "good or even great".
Distilling the book in my words:
Every year companies have to make more money. more than the previous year, and in some companies it is more than the previous quarter.
The dynamics of creating budgets and projections coupled with the personnel that is available causes the following dilemma:
To make more money each person designing next years budget tries to create a more profitable product (or service) or method.
The problem is that this is incremental in nature. How to make more money if you make widget A that is 2x capable?
The safest method (it seems) is to make the widget capable with 4x, and charge a bit more.
Well this process happens again and again . several years down the road the widget will be 10x capable.
But a disruptive technology comes along, it is a mini-widget which (for example) is not in the widget market, is only capable of 2x, but can be created at 20% of the cost of the widget at 2x.
So now the company is producing widgets at 16x and sees a competitor at 2x and laughs...
But in reality this new competitor is carving a new market and has the potential to completely blind side the company.
Tony Zafiropoulos (4/10/07)
While there I was drafted to fix a DVD burn problem ;)
This happens frequently to me, while on 'vacation' I fix something.
It was an interesting problem since the machine was relatively new (1.5 years), yet would not burn DVD's or CD's with most of it's programs.
After some investigation it seemed to be the new IE7.0 install, for some reason that particular DVD drive (I believe a Philips 8701) would have a conflict with IE7.0.
After uninstalling most of the DVD/CD burn software and still not working, uninstalled IE7.0, then it worked.
Odd problem, but this is typical of Microsoft, since IE is so intertwined within the OS there are bound to be problems for any x.0 software.
It just happened that it took me a while to figure this out. - (TonyZ 4/9/2007) It does not seem obvious to uninstall IE7.0 to get your burning process to work ;). But now all is well, my sister-in-law then was able to copy more DVD's for all of the kids hockey pictures etc.
![]()
Eweek article about wireless encryption protocol (WEP) being easy to crack.
WEP was cracked a relatively long time ago (in computer field long time is 2 years ;).
But what makes this significant today is that tools to crack WEP wifi are much easier to come by, and thus it is relatively easy to break the code.
Here is the paper by Erik Tews, Ralf-Philipp Weinmann, and Andrei Pyshkin at Technische Universitaet Darmstadt (Germany) - "Breaking 104bit WEP in less than 60 seconds"
Please do not use WEP for WIFI, use WPA or better yet WPA2(latest version). Tony Zafiropoulos - 4/7/2007
![]()
Oops - another exploit for the microsoft platform - and this time it effects most windows programs (that can load icons or cursors) Determina Security Research found the exploit.
This one is fairly serious, as Microsoft has issued a midmonth, midweek patch (they usually patch once per month and on Tuesday only). (Tony Z 4/6/2007)
![]()
If you have not read "Innovators Dilemma" by Clayton Christensen it is nigh time that you did ;).
Here is a link for a snippet out of the book: CEO Refresher
I noticed that a new edition (2006) came out, I read both previous editions and it looks like an additional 2 chapters were added.
More information that explains why great companies miss out on disruptive technologies...
if you ask me, the latest example (for the next edition;) is youtube, this is where you can place your own videos on the internet allowing others to see them at their leisure.
the reason it works is that the site is Google searchable, and thus more people can find your video, and people eyeballs is what is important.
once Youtube had a significant following something strange started to happen.
There were people that started making a small career out of creating videos on the net. And they actually received some notoriety for it.
Youtube keeps you coming back by not allowing your file to be downloaded, only streamed to the desktops.
This keeps their legitimate visits high, and the site received more free press by crosslinking with blogs and famous online sites (Drudge Report).
Ask this question: Would a media company (Nytimes, cbs, nbc) have the capability to put this together? Capability yes, but not willing to do it.
It does not make sense for a media company to set up a site that is easy to use for their customers to put videos on it... But a media company works on the advertising principle of keeping their medium free while charging advertisers for ads on their medium.
WHY did they not see this coming? The Innovators Dilemma explains this phenomena well. (TonyZ 04/4/2007)
![]()
"Automate Success Not Failure" says Paul Strassmann in Information Payoff - am re-reading it - it is an interesting book written by a CIO/technologist from the 70's copyright 1985.
I like it because it has a lot of interesting information that aplies to any time era. Also to note that many different items have not changed very much.
Also looked at the "IT doesn't Matter" controversy. Nicholas Carr wrote this article.
Summary - Info tech is a commodity, and thus it should not be paid that much attention. Other things should matter more.
People are still talking about this statement, which was published in the Harvard Business Review. It struck a cord with the tech world.
The response has been to say ok, but Business Processes do matter with IT. Or actually let's just change the language and talk about business processes instead of talking about IT.
Sure some of IT has become a commodity, but it is needed in our inter-connected world.
I will give Nicholas Carr credit for saying that IT is not the end all and be all which the 1999 - 2001 tech boom was all about, whenever there is froth there will be people that will not be happy with the situation. And the article (written in 2003) explained the feelings of the time right after the tech boom busted.
Unfortunately I believe he misunderstood the role of IT, and in fact many people still do not get it.
The Book "Good To Great" summarizes it very well: IT is a catalyst, after the business goals and management team is in place.
(Tony Zafiropoulos 03/29/2007)
Here is an excerpt from Mr. Carr's website (link above):
Bill Gates "assailed" my article in a speech at Microsoft's CEO Summit on May 21, saying, "And so when somebody says, to take the extreme quote from the Harvard Business Review article, they say IT doesn't matter, they must be saying that with all this information flow, we've either achieved a limit where it's just perfect, everybody sees exactly what they want, or we've gotten to a point where it simply can't be improved - and that's where we'd object very strenuously." Just to be clear, what the article argues is that we're at the point where any technological improvement in the management of information will be quickly and broadly copied, rendering it meaningless for competitive advantage.
Carr made several points in his article, one of his points that information advantage is brief is ironically because of IT... because IT is so ubiquitous.
He also does not understand how software is developed, the different methods of development (closed or open.
The concept I will concede easily though is that the reason it is easily misunderstodo is because of the complexity of making a project work within a business environment.
![]()
Mean Time to Repair:
The total corrective maintenance time divided by the total number of corrective maintenance actions during a given period of time.
I am going to develop MTTR incident report system for the clients that I currently have.(Tonyz 03/28/07)
Definition Of MTTR
I am trying this new Yahoo Answer site - where people can ask questions and others can answer (for free) My profile is "ctitek" (Tonyz 03/28/07)
![]()
Cool RFID IO tool This is an interresting Python (programming language) toolkit to read RFID (Radio Frequency Identification).
This is an interesting tool to use for reverse engineers.
TonyZ(03/27/07)
![]()
Adobe will not update its creative suites software apps to Vista for free - This is likely due to a significant investment on the part of Adobe.
I know a lot of people are crying themselves to sleep over the significant plight of Adobe - having to spend a lot of R&D money just to keep up with whatever Microsoft does, but the reality is Companies that write software have to make these decisions all the time.
And this time Adobe decided to charge for the compatibility, and I would not expect too many new features in this upgrade. (Tony Z 03/26/2007)
![]()
Alienware overclocks processors and sells them Now I understand how Alienware gets more performance out of their computers than other manufacturers.
Unfortunately this is like playing with fire - since overclocking the CPU is risky when the machine overheats. They did pick the sturdiest piece of the computer pieces, since CPU's typically have 10 year MTBF's (Mean Time Between Failures). But if something goes wrong there is a good chance that nothing will work , and in fact it will look like parts will go bad intermittently.
Sometimes very difficult to diagnose a bad CPU. Probably not too many people around when the PentiumPro had its addition bug (TonyZ 03/23/2007)
![]()
Surge in Hijacked PC's - BBC article about Symantec information
Snippet: More than six million computers world wide are now part of a "bot network", reported security firm Symantec.
Computer users typically do not know that their PC has been hijacked.
More than a third of all computer attacks in the second half of 2006 originated from PCs in the United States, the threat report said.
Most computer users are naive about connecting to the internet, protecting their computers and thus reducing their exposure to criminals which want to send out spam using someone elses infrastructure.
Please ensure that your Anti-virus software is the latest version and buy yourself a seperate device that is your firewall. There is firewall software on your computer but it is not good enough. (Tony Zafiropoulos 3/19/2007)
![]()
Oops - Timezone problems You may see systems that have successfully applied the Windows DST2007 hotfix 931836 but are still operating on old DST rules after March 11. Opening the Time/Date control panel applet and changing the time zone to a new time zone; hitting apply, and changing it back to the original time zone will often correct this problem.
It looks to be dependant on if one uses the TZ environment variable: More information available following link (http://support.microsoft.com/kb/932590/en-us) (TonyZ 03/12/2007)
![]()
Microsoft Daylight saving Time Website - Remember that Daylight Saving Time is changing in the US on 3/11/2007 this year.
Make sure and patch all of your time sensitive computers and applications (Operating systems and Email servers).
.
Or change the time manually :) - this is not a good fix as the systems may change back - depends.
this is sort of like the Y2K patch in the year 1999, except that we had many months to prepare for 12/31/1999 --> 1/1/2000. This time we IT peoples only received a couple of months and patches are still coming out of the vendors.(TonyZ 3/9/2007)
![]()
eweek article about Government website hacked for its linking ability
This is a great explanation: The .gov links are highly coveted, Schrock notes, given that Google and other search engines treat them as "solid gold" because they're only allowed to be used by official government sites in the United States. This automatically elevates a site's ranking in search engines.
more snippets: Thor Schrock, owner of computer repair and services shop Schrock Innovations. Schrock said in his blog that he discovered the hack when he noticed a spam post on his customer support forum that he "normally would have deleted and forgotten about," if it weren't for the fact that the dozens of links in the post led back to a .gov site, "a highly unusual occurrence for this kind of scheme."
The NOAA likely does not have the greatest of administrative help, so it is likely easy to target.
This hack was useful because of the value of a .gov link.
Hopefully this explains a bit more:
If a government website (with .gov extension) has a link on its site to another website this link will be rated higher on Google. (instead of a link that I would create on my website).
Google's perception is that .gov websites that link to other websites are likely useful and valid.
Of course whenever your sole reason for existence is to cheat and lie then do not be surprised when something drastic happens to you.(TonyZ 3/6/2007)
![]()
Please update your Norton Anti-virus "software" --- not just definition files.
I have dealt with two clients now that ran into the smitfraud virus or trojan, but it would have been caught if the person would have just upgraded their software (they did update the definition files, but that is different).
If you have any questions please contact me (Tony Z. 02/28/07)
The computer virus or trojan seems to be not very dangerous (deleting files etc.) just annoying, as it starts to take over more and more resources, sometimes not allowing you to run what you need. It is also called trojan.alemod. Here is a link on Symantec's website for more info.
![]()
Very interesting - VMWare is a virtualization software - allowing Microsoft software to run multiple times on the same hardware - this allows companies to run less hardware in the never ending battle of space in data rooms.
The problem lies that Microsoft does not want to lose any portion of the software market, and it fears that eventually VMWare could take more and more operating system market share, so they have built into its licensing terms (the stuff that you agree to without reading ;) that you have to buy a license for each license that you use even on the same machine. This was not previously the case. The license was per machine. Which with VMWare you could run multiple times.
So effectively Microsoft is driving out the $710mil market that VMWare built for itself - nothing abnormal here if you have been studying Microsoft for the last 15 years like I have. (Tony Z. 02/26/2007)
Quote by VMWare and lawyer:
Two choice quotes: "Microsoft is looking for any way it can to gain the upper hand," said Diane Greene, the president of VMware. And, "This seems to be a far more subtle, informed and polished form of competitive aggression than we've seen from Microsoft in the past," said Andrew I. Gavil, a law professor at Howard University.
![]()
The current question to me is: Should you(I) install Vista?(02/04/2007 - TonyZ
![]()
The Sprint Nextel 4G mobility network will use the company's extensive 2.5GHz spectrum holdings, which cover 85 percent of the households in the top 100 U.S. markets - the most of any wireless carrier in any single spectrum band. To access that network, Sprint Nextel will work with Intel, Motorola and Samsung to incorporate WiMAX technology for advanced wireless communications and help make chipsets widely available for new consumer electronics devices, connecting consumers to the Internet and to each other while providing them with the flexibility to do what they want or need to do regardless of time or place.
![]()
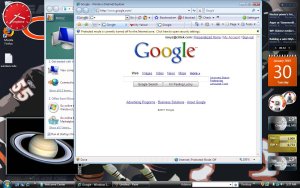
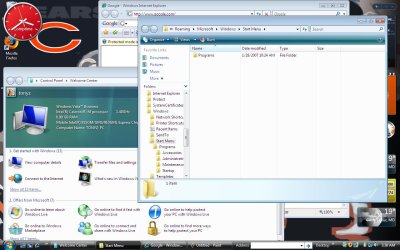
If you notice the bottom picture I opened the new Windows Explorer look and the new windows control panel. When your mouse moves over to the edges of windows explorer and there are more files or folders to be viewed the program automatially moves to it.
Discovered: February 21, 2006
Updated: February 21, 2006 01:50:27 PM ZE9
Also Known As: Olympic Torch hoax [Sophos]
Type: Hoax
P.S. most of these hoaxes usually say they will burn a hole in your hard dribe or melt the hard drive or something... This is not possible - it is not possible to "melt" or "burn a hole" in a hard drive.(Tony Zafiropoulos 01/15/2007)
Adobe PDF flaw - Informationweek article
A PDF can be exploited to run code that will control your computer. - This is very bad as many companies have pdf files - and if their websites get compromised with 1 or two pdfs then we can have legitimate companies being unwitting accomplices in crime.
For now this exploit is only possible in Mozilla's Firefox 1.5 and Opera 9.10 browsers. - Please update your browsers as soon as possible if you have Firefox or Opera. Microsoft Internet Explorer is not effected (generates an error). Tony Zafiropoulos (1/4/2007)
Have you noticed a surge in spam? Eweek article Eweek pinpointed Russian "Bot Herders" as the culprits. This is just another in vogue term for "criminal". These criminals have figured out a way to control 70,000 computers to spew spam out to the internet. Tony Zafiropoulos 12/27/2006
 This image from http://hackles.org/spam/ A picture says a thousand words... but what does a spambot look like? ;)
This image from http://hackles.org/spam/ A picture says a thousand words... but what does a spambot look like? ;)
 hard drive picture from helpwithpcs.com
hard drive picture from helpwithpcs.com
 Fixvirus.com Scion at the Sevens Building in Clayton ( we fix computers as well - not just viruses).
Fixvirus.com Scion at the Sevens Building in Clayton ( we fix computers as well - not just viruses).
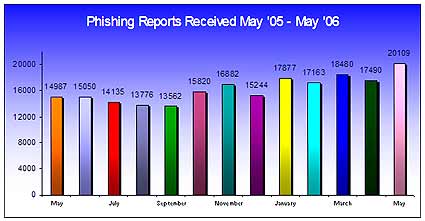
Anti-Phishing Working Group ReportNumber of unique phishing reports in May 2006 = 20,109
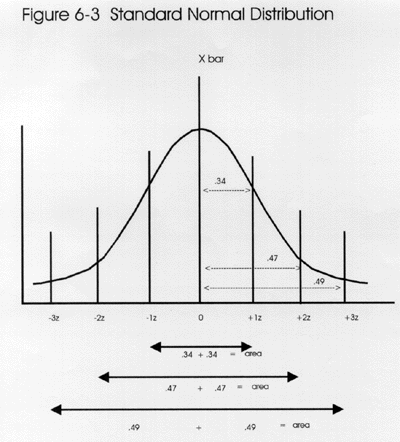 , and where 2sigma is 95.45% of the area under the curve. .9545 is more accurate than image(between -2sigma and +2 sigma on the x-axis).
, and where 2sigma is 95.45% of the area under the curve. .9545 is more accurate than image(between -2sigma and +2 sigma on the x-axis).
top - 10:42:53 up 385 days, 19:01, 2 users, load average: 0.10, 0.03, 0.01
Yes, it is a Linux system... Of course 385 days without rebooting also depends on clean power. TonyZ 04/07/06
new Microsoft IE (Internet Explorer) exploit has been created only 24 hours after a denial of service (DOS) bug was found Eweek article 03/26/06
Anti-virus information Symantec latest Virus list list: March 1st new virus is Beagle
Symantec Hoax list: Do not propagate the hoax 'warnings'. When receiving an email to send to 10 friends check this list first.
McAfee virus list - includes virus map'
![]()
An excellent explanation of the Benefits of Open Source:www.theaceorb.com benefits page Just checked it out, and still a very good reference of how open source programming works ;). 03/2/2006 TonyZ
The Business case for Open Source
SANS Institute incidents.org CID: Consensus Intrusion Database
SANS.org is an excellent group that looks at many security related issues... CID gives a snapshot of current hacker / worm activity on the net.
Anti-Virus centers that we use to control viruses.
McAfee Virus Information Library
This database contains information on more than 50,000 known viruses, including how they work and how to kill them.
Symantec AntiVirus Research Center
Symantec's security update web page - extensive resources and latest information on viruses on the Internet.
Washington Post Chronological History of the Computer Virus